Lesson Learned from Vision Pro as a Cybersecurity Veteran — Part I — Classical Cryptography

As a marketing head in the cybersecurity industry for 8 years, confronting painstaking situations resulting from, not useless, but unusable technology is not a surprise. We usually deal with the “how to use it” issue. It’s not that technology is terrible. Instead, technology is too advanced to create values. Enterprises often have a hard time applying cutting-edge technologies, thus failing to develop valuable products.
Here I would like to discuss my experience in a cybersecurity company specializing in cryptography. I hope what I’ve been through can resonate with the concept of “spatial computing” in the field of VR/MR.
Brief Explanation of Cryptography
Cryptography is a domain only gurus can master. Our company happens to rely heavily on cryptography to develop products and solutions. Nevertheless, we had difficulties leveraging talented cryptographers for our product development. Imagine it as a company specializing in spatial computing but failing to create useful or valuable products. That’s how things went back then. In this article, I would like to explain what cryptography is.
Classified Intelligence — Key to Shaping the Battlefield
War has never ceased throughout history. Kings wage war for their empires, generals fight for power, and the crucial factor in achieving victory is as the timeless maxim in “The Art of War” by Sun Tzu states: “Know thyself, know thy enemy; a hundred battles, a hundred victories.” Understanding the enemy is the path to triumph, making enemy intelligence a pivotal asset in warfare. Conversely, to prevent the enemy from obtaining our own intelligence, rendering “them unaware” becomes an essential strategy.
To achieve this state of “unawareness,” our forces manipulate the content of the information before transmission. This process is known as “encryption.” Even if intercepted by the enemy, the content remains incomprehensible. As for “knowing thy enemy,” our forces intercept enemy intelligence. If the intelligence is encrypted, our analysts undertake the task of “cracking” the encryption — deciphering the methodology and identifying vulnerabilities. If successful, this process leads to the restoration of the encrypted message’s content and subsequent interpretation, referred to as “decryption.

In 45 BC, Julius Caesar, the Emperor of Rome, employed a uniform letter shift to encrypt the content of letters exchanged with his generals¹. In the 16th century AD, Mary, Queen of Scots, also employed letter substitution to encrypt letters pertaining to a conspiracy to assassinate Queen Elizabeth I of England². However, the encryption method was eventually deciphered, and it is rumored that Mary’s involvement led to her execution by Queen Elizabeth³. One of the most notable modern cases occurred during World War II when the German military used a machine called Enigma⁴ to encrypt their messages. Even if intercepted, the content of the messages remained indecipherable to the enemy⁵.
During that time, Alan Mathison Turing, a key figure in the British intelligence apparatus, developed the Turing-Welchman Bombe⁶, a cryptanalysis technique to analyze the results of Enigma encryption. This significantly shortened the time required for decryption and made a significant contribution to the cessation of hostilities. The disciplines of “encryption and decryption” and “cryptanalysis” are collectively known as “cryptography” and “cryptanalysis.”
From Classical to Modern: Military and Political Encryption Techniques Throughout History
From the past’s Caesar cipher to substitution ciphers and Enigma, in the realm of communication, both parties involved needed to generate a common “shared secret key” before transmitting messages. Only through this shared secret key could the messages be encrypted and decrypted.

The drawback of sharing keys is the difficulty in key management. For instance, when a group consists of one hundred individuals, each communicating confidential messages with ninety-nine others, in order to prevent interception and decryption by third parties, these ninety-nine keys must not be duplicated. This means that each person needs to manage ninety-nine distinct keys, resulting in a significant allocation of resources and high management costs.
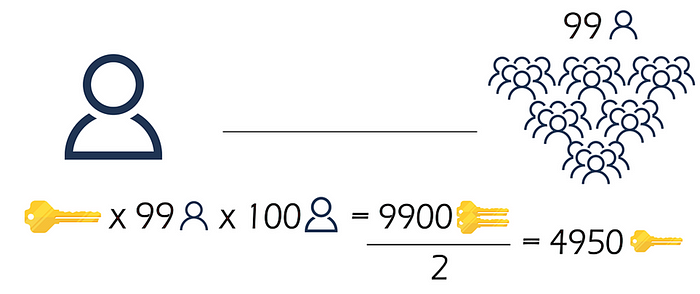
The drawback of sharing keys is the difficulty in key management. For instance, when a group consists of one hundred individuals, each communicating confidential messages with ninety-nine others, in order to prevent interception and decryption by third parties, these ninety-nine keys must not be duplicated. This means that each person needs to manage ninety-nine distinct keys, resulting in a significant allocation of resources and high management costs.
Another drawback lies in the limitations of key distribution in shared keys. How can one ensure that shared keys are securely distributed to the intended recipients? If there were a secure way of distributing keys, why not directly transmit the confidential messages? When two individuals who have never met need to exchange confidential messages, the farther apart they are, the greater the risk of leaks during key distribution. Taking these factors into account, cryptographers have continued researching solutions, and there was a significant breakthrough in the 1970s with the birth of the “public-key cryptographic system,” which changed the rules of the game.
[1]: Luciano, D., & Prichett, G. (1987). Cryptology: From Caesar Ciphers to Public-Key Cryptosystems. The College Mathematics Journal, 18(1), 2–17. doi:10.2307/2686311
[2]: Page of ciphers used by Mary Queen of Scots, c.1586 (SP 53/22 f.1) https://www.nationalarchives.gov.uk/education/resources/elizabeth-monarchy/ciphers-used-by-mary-queen-of-scots/
[3]: Historical Encryption: The Babington Plot https://www.thesslstore.com/blog/the-babington-plot/
[4]: Enigma — The International Museum of World War II https://museumofworldwarii.org/collection/enigma/
[5]: Enigma: Why the fight to break Nazi encryption still matters https://www.cnet.com/news/enigma-why-the-fight-to-break-nazi-encryption-still-matters/
[6]: The British Bombe — Turing-Welchman Bombe https://www.cryptomuseum.com/crypto/bombe/

